How to set up the system security by using the IP Blacklist and the Security incidents options
Ozeki Phone System has several tools to protect the PBX from malicious intents. You can use the IP Blacklist and the Anti-Hacking feature for the purpose to do not let particular IP addresses to access to the PBX.
This topic will introduce the IP Blacklist and the Security incidents elements of Ozeki Phone System.
1. IP Blacklist
The IP Blacklist is a list of IP addresses, which are not able to reach the PBX for a previously set period of time.
-
There are two ways to add IP address(es) to this list:
-
adding the IP address(es) manually,
- using the built-in Anti-Hacking feature.
This guide shows how to add IP address(es) to the IP Blacklist manually. To learn more about the Anti-Hacking feature, please click here
Step 1: Getting to the IP Blacklist panel
In the PBX features menu, click the Preferences submenu as Figure 1 shows:
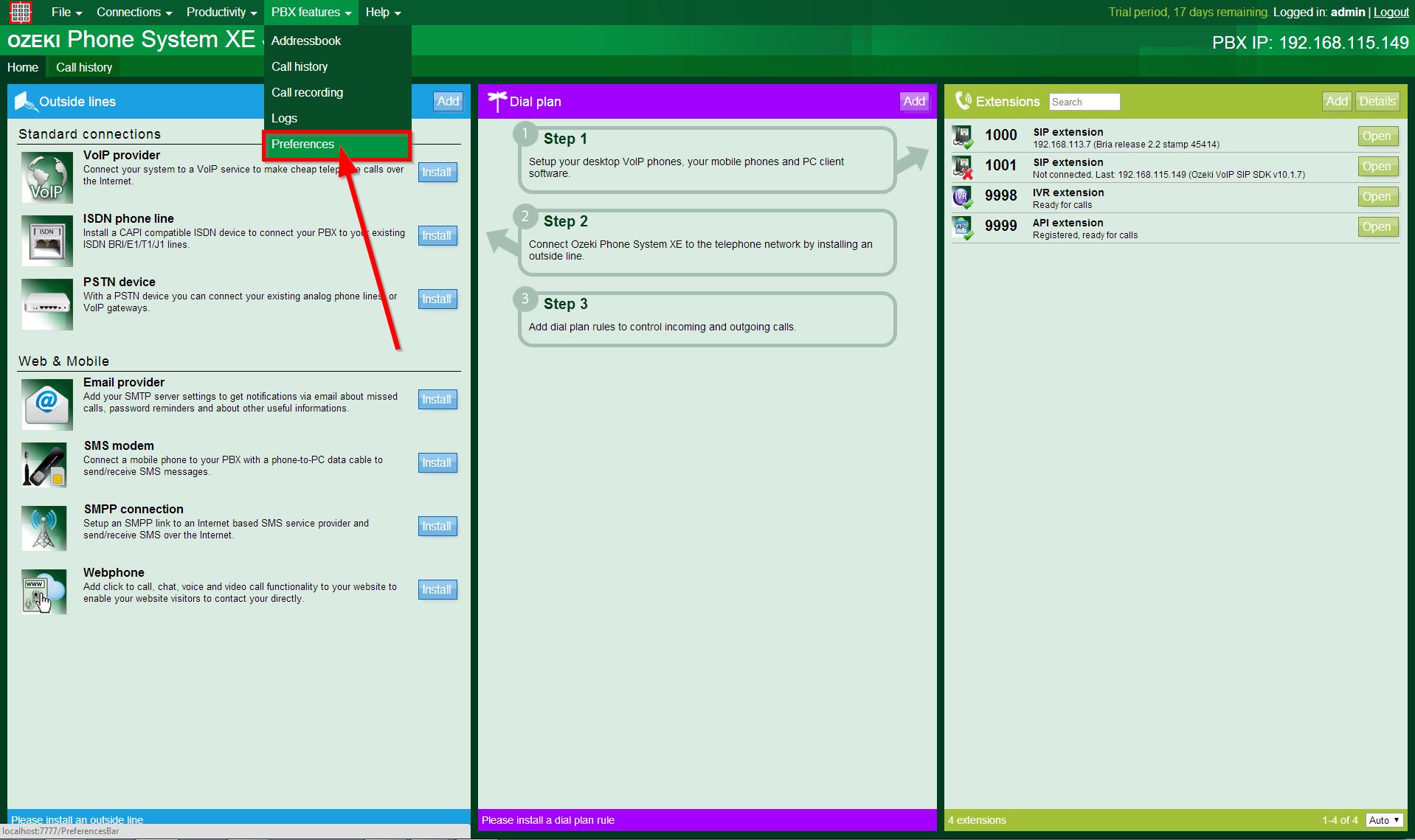
Here, You have several configuration options, such as Security incidents, IP Blacklist etc. Since You would like to manage the blacklist, You need to click on the IP Blacklist option (Figure 2):
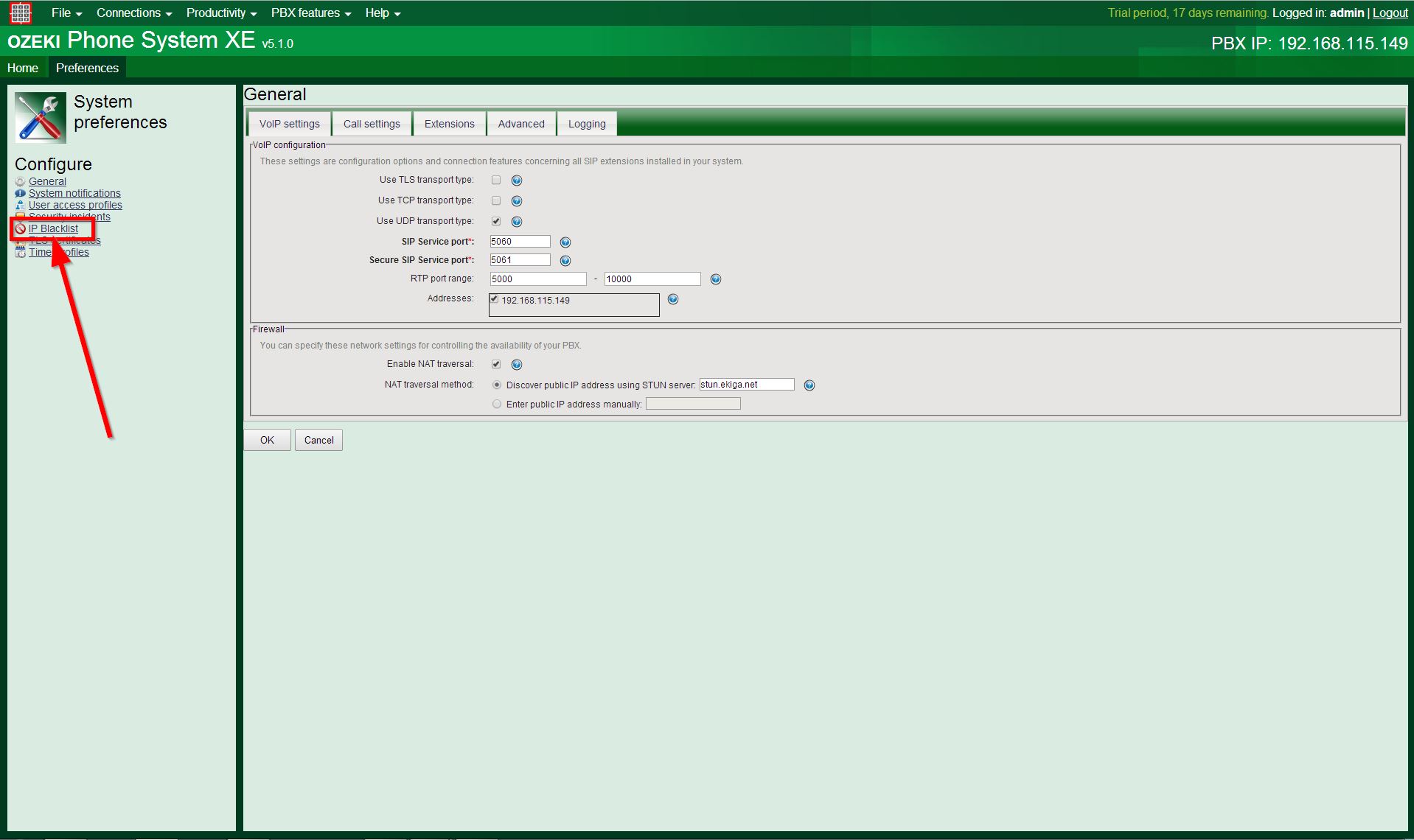
Step 2: Manually adding IP address(es) to the blacklist
At the IP Blacklist panel You can add IP address(es) to the blacklist, or You can manage the previously added ones. To add a new entry to the list, You need to click on one of the Add buttons, as Figure 3 shows.
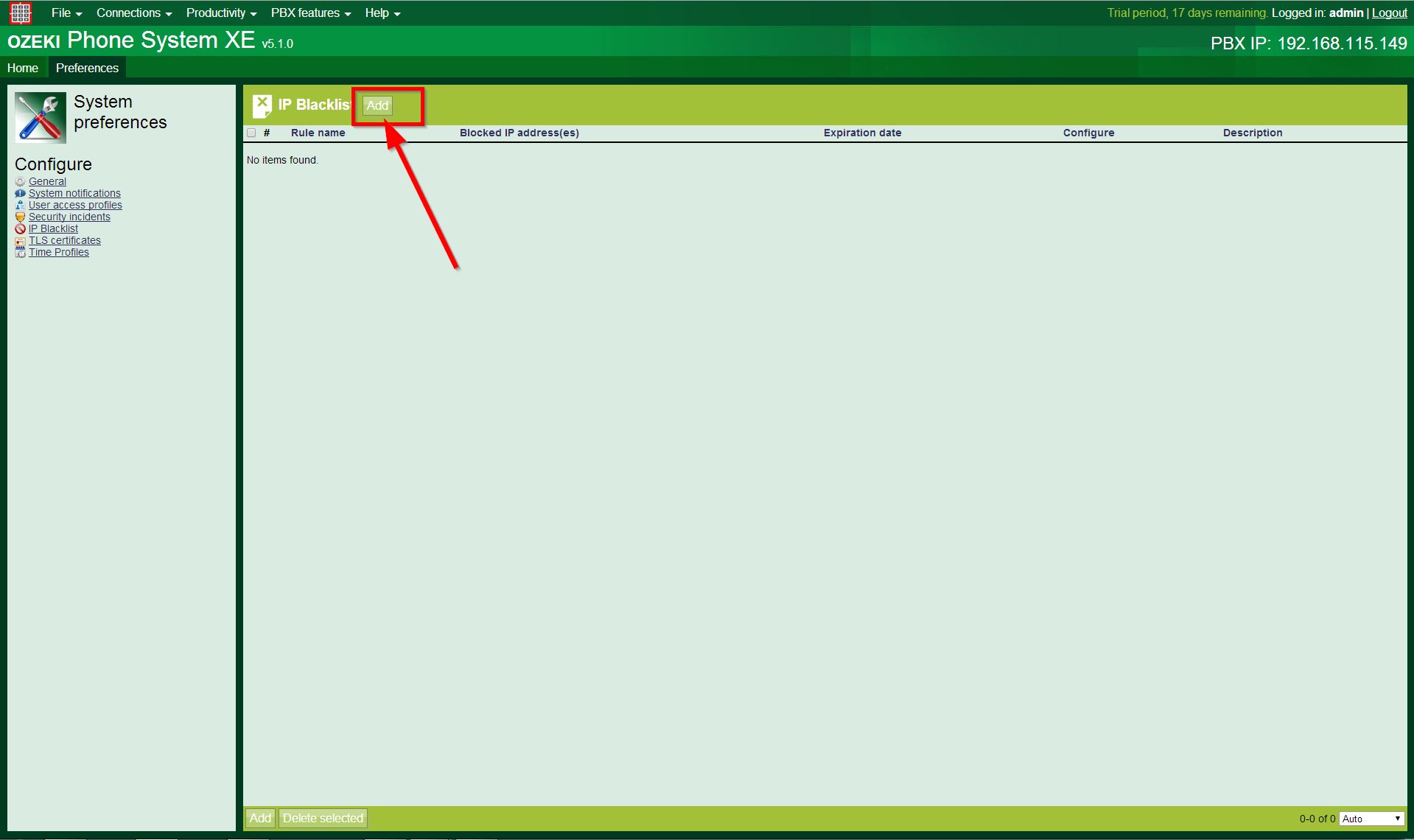
The following form will appear, as Figure 4 shows:
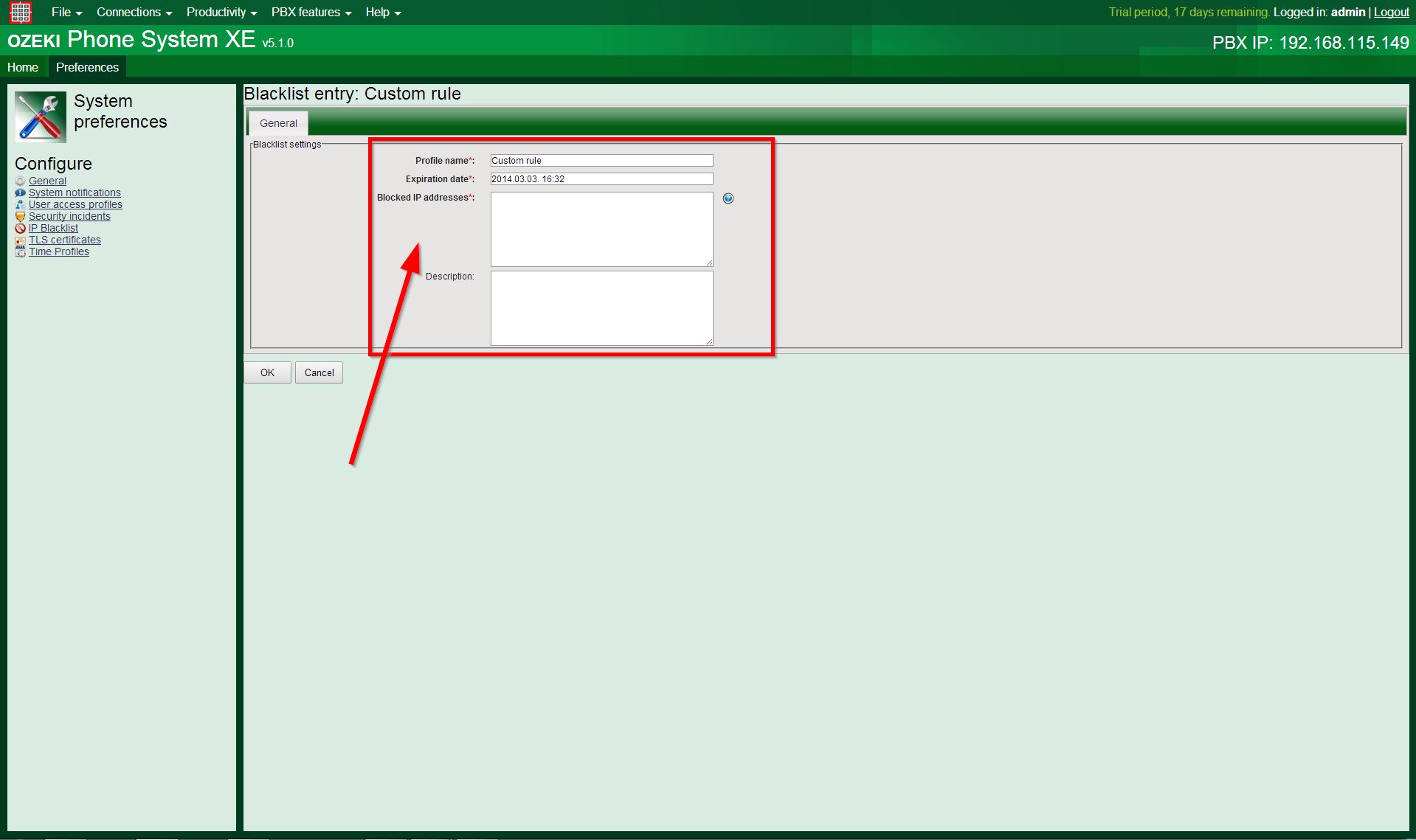
The first three of the settings must be set (these are indicated on the screen with bold label and a red "*" character at the right of them), and one of them is optional:
- Profil name: a text to display short information about the entry.
- Expiration date: within this field, the entry’s expiration’s time and date can be set. Until the end of that date, it is not possible to use the PBX with the IP addresses, which ones were set at the "Blocked IP addresses" field.
- Blocked IP addresses: here, You can enumerate one or more IP address(es) (one per line), or You can provide IP address ranges, for example: "192.168.0.1-192.168.0.100". These IP addresses are not allowed to use the PBX before the given expiration date ends.
- Description: it is not necessary to fill this field, but sometimes it can be really useful; it’s a note, which is usually used for storing information about the reason of the blacklisting, or about the person or computer, who was added to the blacklist. These are only examples, You can write here any information You would like to, as a note for yourself.
Step 3: Managing the entries
If the list contains any entries, You can find those under the IP Blacklist option (where You were adding the new ones). Here, You can modify the previously set parameters, or You can even delete them, or the whole entry. There is a way to delete more entries in the same time (see below, at the selector checkbox column). Figure 5 shows us a blacklist, which contains an entry.
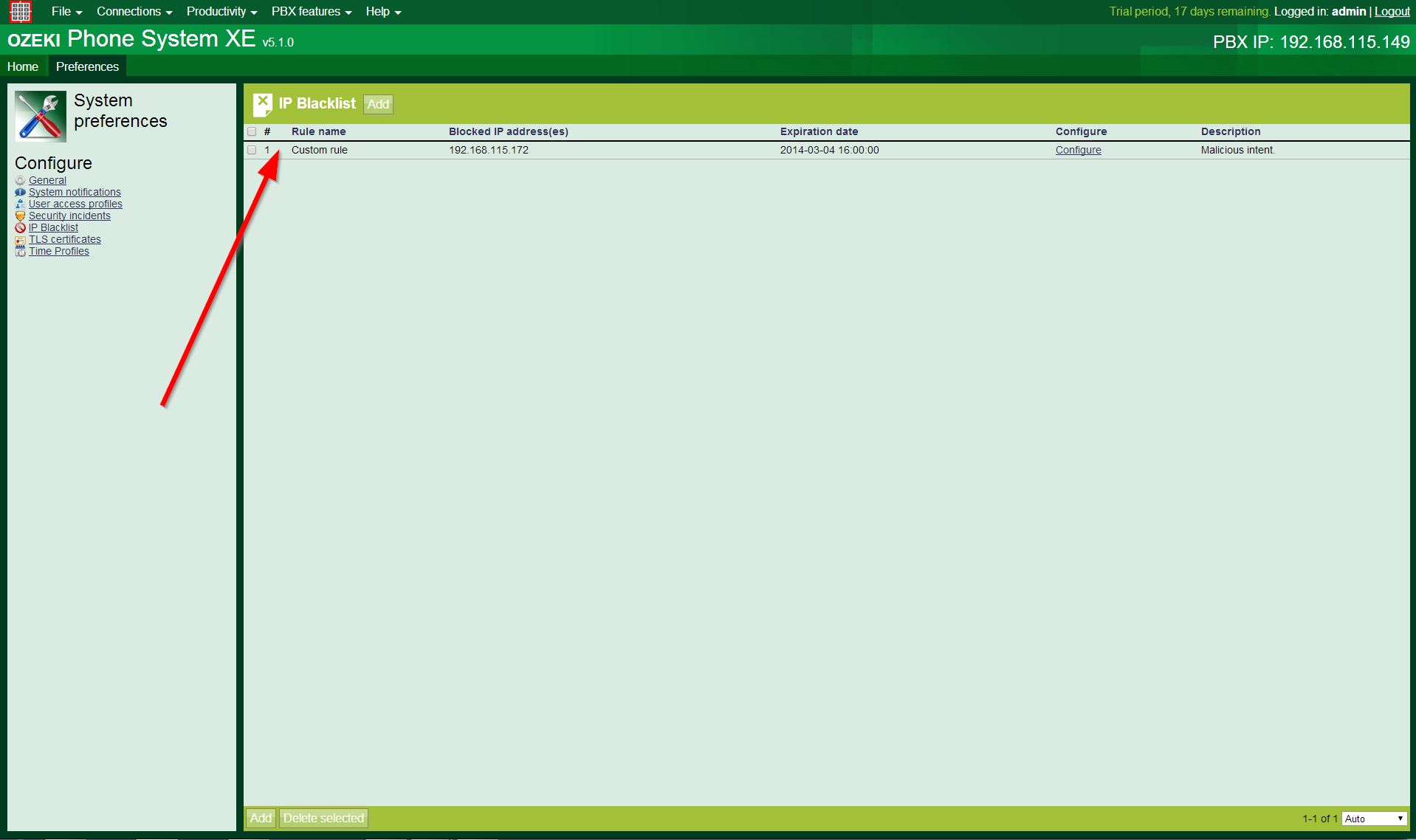
Every row means an entry, and You can find here the previously set informations under the column names, and as You can see, these informations in the example entry were given at the adding as:
- Profile name: Custom rule
- Expiration date: 2014-03-04 16:00:00
- Blocked IP addresses: 192.168.115.172
- Description: Malicious intent.
There are three new columns on the screen:
- selector checkbox: You can delete more entries from the list in the same time, by checking the checkboxes at the correct rows, and clicking on the Delete selected button, which is at the bottom of the screen, next to the nether Add button.
- row number: the rows are being counted with an integer number, to make it easier to navigate between the entries.
- configure: by clicking on the configure option at the entry’s row, You will find yourself on a form similar to the Blacklist settings (shown by Figure 4), but the fields are not empty this time; they are filled with the previously given settings. You can edit these settings here.
If the list contains more entries, You can sort them by the columns. To do this, You need to left click on the column’s name, and to reverse the order of the sorting, click the column’s name once again.
At the bottom right corner of the screen, You can find how many entries does the list have, and which ones are being shown (by the pages number). There, You can also set how many entries should be shown per page.
Notifying the user about being on the IP Blacklist
The access will be denied until the expiration date ends, if You try to reach the PBX’s GUI from an address, which is on the Blacklist. In this case, You will see something similar to Figure 6.
You are not able to access to the PBX with any of the extensions, if your IP address is on the blacklist. Usually, You are just getting a message about the failed registration, but if You are using the tools of the Ozeki VoIP SIP SDK to develop your softphone, You can set the application to inform the user about the reason of the failure, like the Demo Application does on Figure 7:
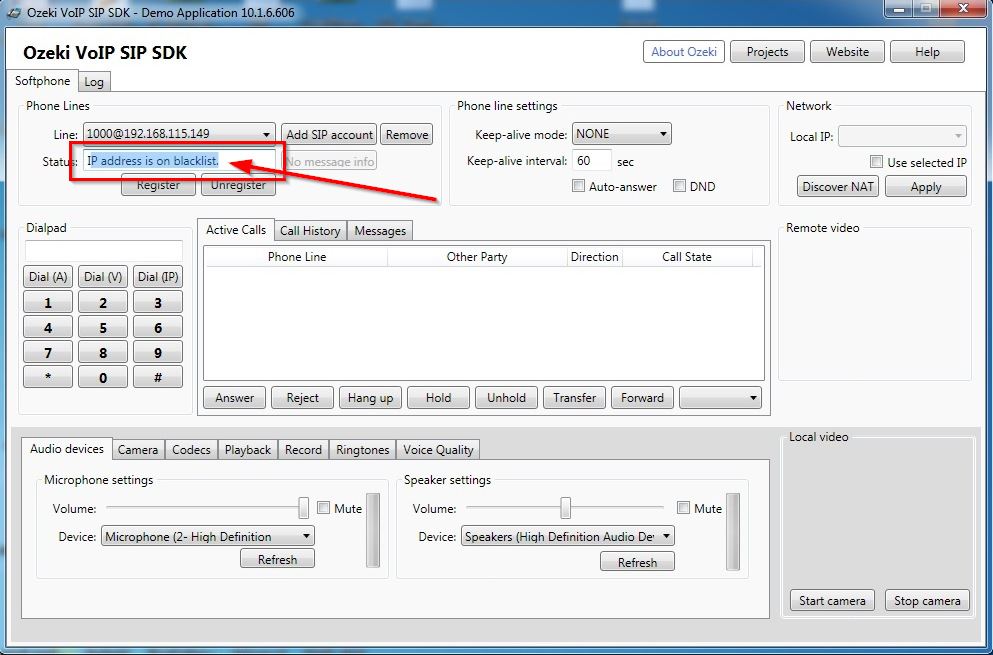
If You have installed Ozeki VoIP SIP SDK, the Demo Application is located in the Examples folder
in the installation directory. You can download the SDK at: Ozeki VoIP SIP SDK.
If You don’t want to develop a new softphone, You can try an existing one by downloading Ozeki XD Phone at:
Ozeki XD Phone.
This is a free softphone, which is also capable to make 2D and 3D video calls.
2. Security incidents
Ozeki Phone System provides options to handle the events, when there is one or more failed login attempt, authentication request or unanswered challenge requests. With setting these system security parameters, You can also defend the PBX from malicious intents.
This guide introduces the available options, and shows how to set the system security parameters for this purpose.
Step 1: Getting to the Security incidents panel
In the PBX features menu, click the Preferences submenu as Figure 8 shows:

Here, You have several configuration options, such as Security incidents, IP Blacklist etc. You would like to learn about the Security incidents, so You need to click on the Security incidents option (Figure 9).
Step 2: Setting the system security parameters
At the Anti-Hacking form, there are several options, which can be set:
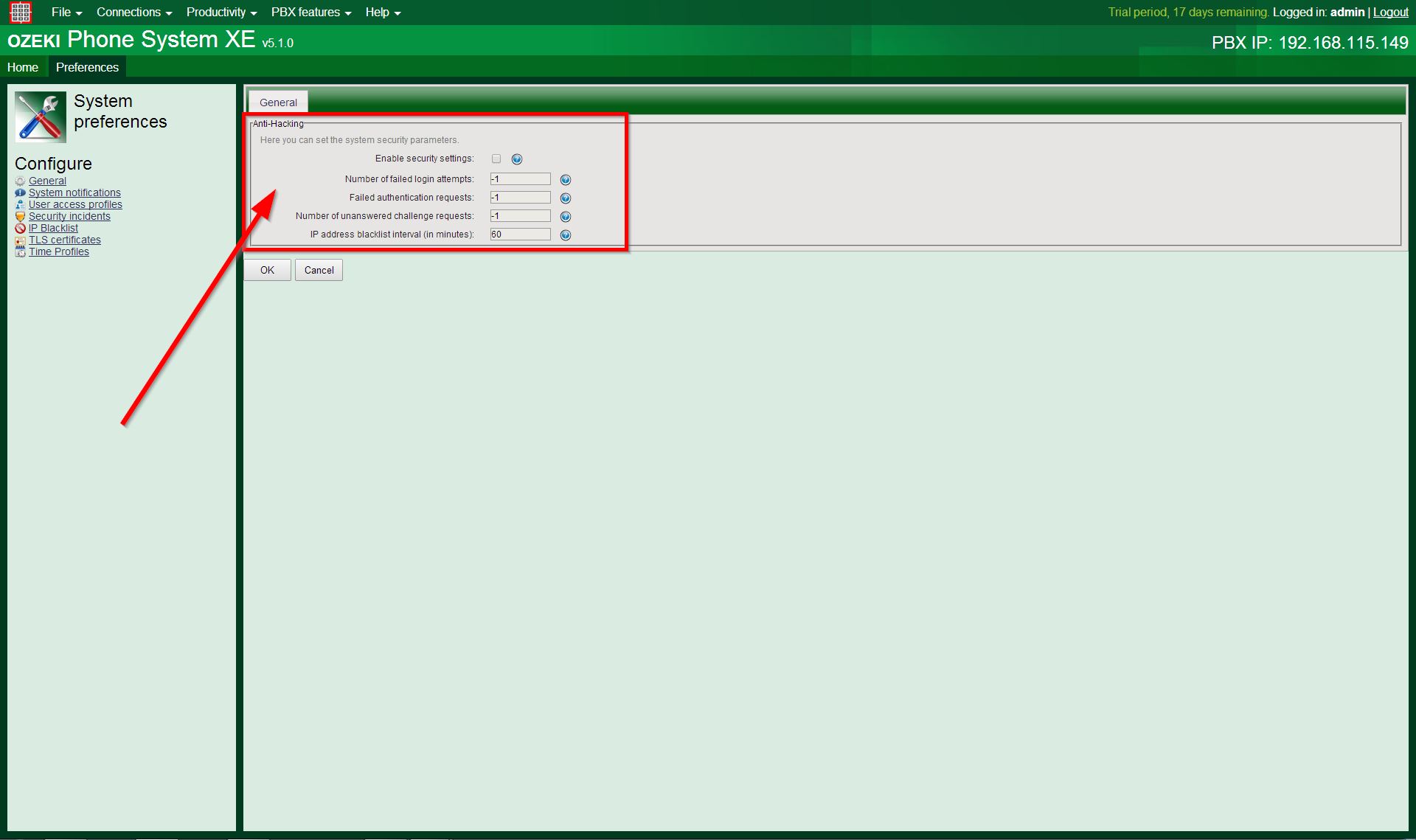
- Enable security settings: this checkbox needs to be checked, if You want the system to create security statistics for the PBX and the SIP extensions. If the checkbox is checked, You can set the followings with numeric values:
- Number of failed login attempts: if the number of failed login attempts on the PBX’s configuration layout exceeds this value within a period of time, the IP address will be put into the Blacklist.
- Failed authentication requests: if the number of failed authentication requests originating from a SIP account exceeds this value within a period of time, the IP address will be added to the Blacklist.
- Number of unanswered challenge requests: this is the amount of incoming SIP messages to the server, which the Ozeki Phone System will tolerate within a period of time. After this, the IP address will be put into the blacklist.
- IP address blacklist interval (in minutes): the time interval, while the IP address will be in the Blacklist.
You can write the "-1" value into the fields, which means: never add the IP address to the Blacklist by the current reason.
For more information about the IP Blacklist, please click here
.
After the parameters are set and the OK button is clicked, the Anti-Hacking feature starts to do its job.
You can try these options by using a softphone. If You have installed Ozeki VoIP SIP SDK, the Demo Application is
located in the Examples folder in the installation directory, or You can even develop your own softphone with
the tools of the SDK. You can download the SDK at: Ozeki VoIP SIP SDK.
If You don’t want to develop a new softphone, You can try an existing one by downloading Ozeki XD Phone at: Ozeki XD Phone. This is a free softphone, which is also capable to make 2D and 3D video calls.
If you have any questions or need assistance, please contact us at info@ozekiphone.com
People who read this also read...
